Blog
Understanding Device Authentication Codes for Secure Access
Device authentication codes are popping up everywhere whenever you try to log in or make a secure connection. Most people think a password is enough and never give these codes a second thought. But the real shock is that device authentication codes are now weaving in physical device fingerprints and machine learning to create security so tough that even if a hacker steals your password, it is nearly impossible to break through. This changes everything you know about digital safety.
Table of Contents
- What Are Device Authentication Codes?
- Why Device Authentication Codes Matter In Security
- How Device Authentication Codes Work: The Technology Behind Them
- Key Concepts Related To Device Authentication Codes
- Practical Applications Of Device Authentication Codes In Everyday Use
Quick Summary
| Takeaway | Explanation |
|---|---|
| Device authentication codes enhance security. | They serve as unique identifiers, ensuring only authorized devices access systems and networks. |
| Dynamic codes provide real-time verification. | These codes change frequently, adding layers of security that make unauthorized access more difficult. |
| Integration with IoT protects smart devices. | Device authentication codes secure connections in smart homes, preventing unauthorized access to IoT devices. |
| Multifactor authentication minimizes risks. | Using device authentication as part of multifactor mechanisms significantly lowers the likelihood of security breaches. |
What are Device Authentication Codes?
Device authentication codes represent a critical security mechanism designed to verify and authorize access to digital systems, networks, and applications. These specialized codes serve as a unique digital fingerprint that confirms a specific device’s identity and legitimacy before granting system entry.
Core Principles of Device Authentication
At their fundamental level, device authentication codes operate as cryptographic tokens that establish trust between a device and a secure network. The primary goal is to prevent unauthorized access by creating a robust verification process that goes beyond traditional username and password protocols. NIST guidelines emphasize these codes as a crucial component of multi-factor authentication strategies.
Key characteristics of device authentication codes include:
- Unique generation for each specific device
- Time-sensitive and often dynamically changing
- Cryptographically secure and difficult to replicate
- Linked to specific hardware or software identifiers
Technological Mechanics of Authentication
The technological infrastructure behind device authentication codes involves complex cryptographic algorithms that generate and validate unique identifiers. These codes typically combine multiple elements such as device serial numbers, hardware signatures, installed software configurations, and randomly generated encryption keys. When a device attempts to access a secure system, it must present its authentication code, which is then cross-referenced against a trusted database to confirm its legitimacy.
Understanding device authentication codes requires recognizing them as more than simple passwords. They represent a sophisticated security layer that protects digital ecosystems by ensuring that only verified and authorized devices can establish network connections. The intricate process involves generating mathematically complex codes that are virtually impossible to predict or reproduce without possessing the original device’s precise configuration.
Here is a table summarizing the core characteristics and features of device authentication codes for quick reference.
| Characteristic | Description |
|---|---|
| Uniqueness | Each code is uniquely generated for a specific device. |
| Dynamic Generation | Codes frequently change and are often time-sensitive. |
| Cryptographic Security | Based on advanced cryptographic algorithms, making replication extremely difficult. |
| Hardware/Software Linkage | Codes are tied to specific hardware or software identifiers on the device. |
| Multi-factor Integration | Commonly used in multifactor authentication alongside other verification methods. |
| Real-time Verification | Authentication often happens in real time to block unauthorized access attempts. |
| Contextual Adaptation | Codes may account for device location, behavior, and hardware signatures for added security. |
Why Device Authentication Codes Matter in Security
Device authentication codes represent a sophisticated cybersecurity strategy designed to protect digital assets, personal information, and network infrastructure from increasingly complex and evolving cyber threats. By establishing a robust verification mechanism, these codes create multiple layers of defense against unauthorized access and potential security breaches.
Preventing Unauthorized Digital Access
In an era of escalating cyber risks, device authentication codes serve as a critical barrier against potential security intrusions. The U.S. Department of Commerce emphasizes that multi-factor authentication significantly reduces the risk of unauthorized system entry by requiring multiple verification steps. These codes go beyond traditional password protection by introducing dynamic, device-specific verification that makes systematic hacking exponentially more challenging.
Key security advantages include:
- Blocking automated attack attempts
- Creating unpredictable authentication sequences
- Generating unique identifiers for each device interaction
- Establishing real-time verification mechanisms
Comprehensive Threat Mitigation
Device authentication codes function as an intelligent security mechanism that adapts to emerging digital risks. They analyze multiple contextual factors beyond simple credential matching, including device location, hardware signatures, and behavioral patterns. This sophisticated approach means that even if a password is compromised, unauthorized users cannot easily bypass the additional cryptographic barriers.
The strategic implementation of device authentication codes transforms digital security from a reactive to a proactive model. By continuously verifying device legitimacy through complex algorithms and dynamic code generation, organizations can create resilient protection frameworks that anticipate and neutralize potential security vulnerabilities before they can be exploited.
How Device Authentication Codes Work: The Technology Behind Them
Device authentication codes leverage advanced cryptographic technologies to create secure, dynamic verification mechanisms that protect digital systems from unauthorized access. These sophisticated systems transform traditional security approaches by integrating complex mathematical algorithms and unique hardware characteristics.
Cryptographic Generation Processes
Researchers exploring device authentication technologies have developed intricate methods for generating unique identification codes that are virtually impossible to replicate. The process involves multiple layers of cryptographic generation, including radio frequency signal analysis, deep learning algorithms, and hardware-specific fingerprinting techniques. These methods create dynamic authentication tokens that change with each access attempt, making systematic breaches exponentially more difficult.
Key technological components include:
- Advanced signal processing algorithms
- Machine learning-based pattern recognition
- Hardware-specific signature extraction
- Probabilistic verification models
Hardware and Software Integration
Device authentication codes operate at the intersection of hardware and software technologies, utilizing Physical Unclonable Functions (PUFs) that exploit microscopic manufacturing variations in electronic components. These unique physical characteristics serve as an intrinsic identifier, creating a mathematical fingerprint that cannot be duplicated or artificially reproduced.
The authentication process involves complex computational techniques that analyze multiple contextual factors simultaneously. By combining hardware signatures, behavioral patterns, and cryptographic algorithms, these systems create a multi-dimensional verification approach that goes far beyond traditional password-based security methods. The result is a robust, adaptive security mechanism that can instantly detect and prevent unauthorized access attempts while maintaining seamless user experience.
Key Concepts Related to Device Authentication Codes
Device authentication codes represent a sophisticated approach to digital security that integrates multiple technological and conceptual frameworks to protect digital ecosystems. Understanding these codes requires exploring the intricate relationship between cryptographic principles, technological infrastructure, and security methodologies.
Authentication Factors and Verification Methods
The National Institute of Standards and Technology defines authentication as a process involving multiple verification factors that collectively establish a robust security mechanism. These factors create a comprehensive approach to verifying digital identities through diverse verification strategies.
Key authentication factors include:
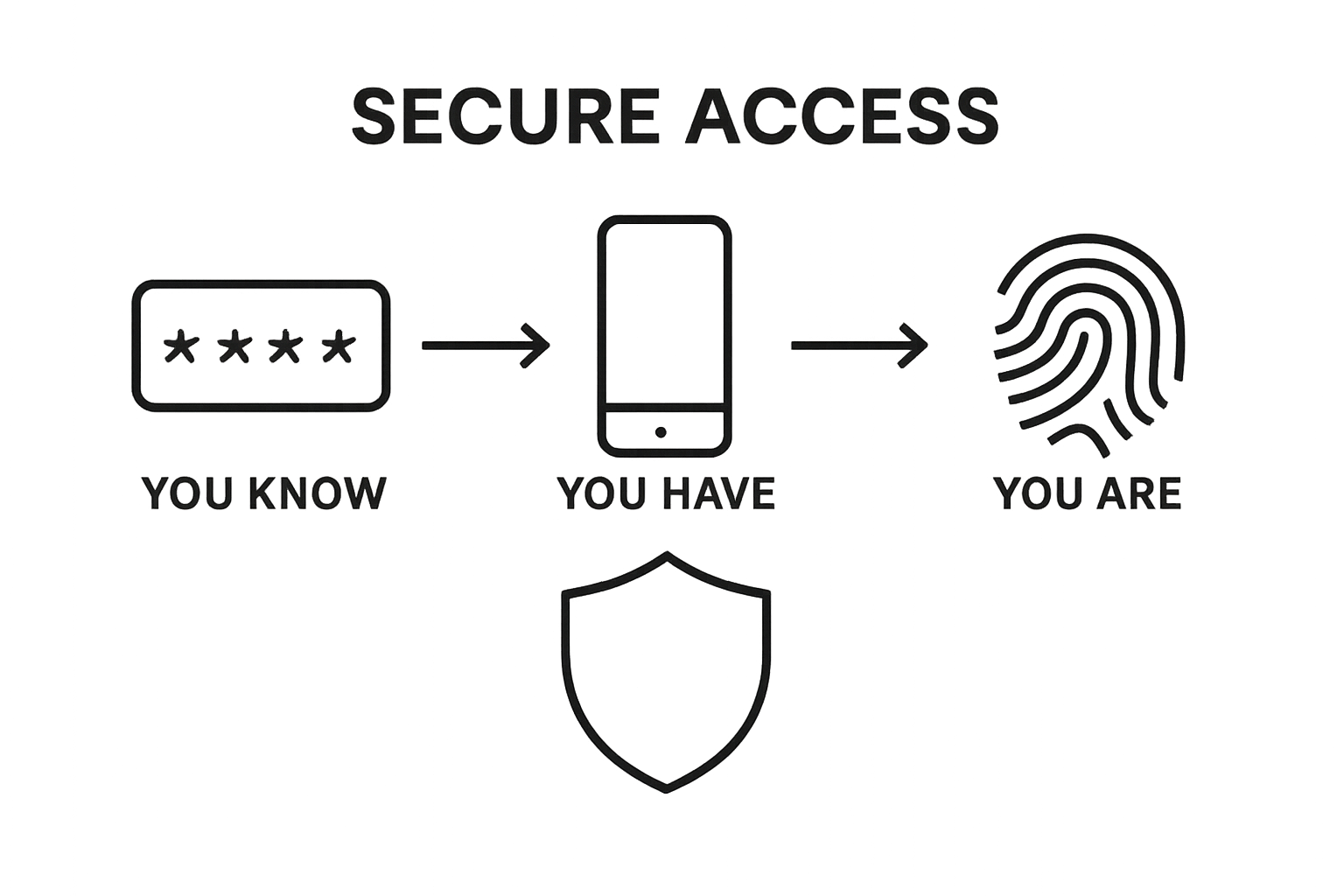
- Something you know (passwords, secret questions)
- Something you have (physical devices, cryptographic tokens)
- Something you are (biometric data like fingerprints)
- Somewhere you are (location-based verification)
- Something you do (behavioral patterns)
Technological Infrastructure of Authentication
The technological foundation of device authentication codes involves complex systems that generate and validate unique digital identifiers. These systems combine multiple layers of security, including hardware-specific signatures, cryptographic algorithms, and dynamic verification protocols. By integrating sophisticated mathematical models with real-time computational analysis, authentication technologies create intelligent security frameworks that adapt to emerging digital threats.
Beyond traditional security mechanisms, device authentication codes represent an evolving approach to digital protection. They transform security from a static, password-dependent model to a dynamic, context-aware system that continuously verifies device legitimacy through multiple interconnected verification channels. This approach ensures that access is granted only after comprehensive, multi-dimensional validation has occurred.
The following table compares the different types of authentication factors mentioned in the article, clarifying their definitions and examples for easier understanding of multifactor authentication.
| Factor Type | Definition | Example |
|---|---|---|
| Something you know | Information only the user should know | Passwords, secret questions |
| Something you have | Physical item in the user’s possession | Phones, cryptographic tokens, devices |
| Something you are | Biometric characteristic unique to the user | Fingerprint, facial recognition |
| Somewhere you are | User’s physical or network location | Device location-based authentication |
| Something you do | Behavioral or activity-based identifier | Typing rhythm, swiping gestures |
Practical Applications of Device Authentication Codes in Everyday Use
Device authentication codes have rapidly evolved from theoretical concepts to practical security solutions integrated into numerous aspects of daily digital interactions. These sophisticated verification mechanisms now play a critical role in protecting personal data, securing digital transactions, and maintaining the integrity of interconnected technological ecosystems.
Internet of Things and Smart Home Security
Research exploring device authentication technologies reveals the expanding role of authentication codes in managing smart home environments. Modern IoT devices leverage unique electromagnetic and radio frequency signatures to create robust security frameworks that protect against unauthorized access. These technologies enable intelligent systems to verify device identities in real-time, ensuring that only authorized devices can interact within home networks.
Practical applications in smart home contexts include:
- Securing wireless network access points
- Authenticating smart home appliances
- Preventing unauthorized device connections
- Monitoring and controlling IoT device interactions
- Detecting potential security breaches instantly
Digital Transaction and Personal Data Protection
Device authentication codes have become fundamental in protecting financial transactions, personal communications, and sensitive digital interactions. By generating unique, dynamic verification tokens, these technologies create multiple layers of security that adapt to emerging digital threats. The authentication process goes beyond traditional password systems, incorporating contextual information such as device location, usage patterns, and hardware signatures.
The implementation of these advanced authentication mechanisms transforms digital security from a reactive to a proactive approach. Users can now benefit from intelligent systems that continuously verify device legitimacy, providing unprecedented protection against sophisticated cyber threats while maintaining seamless and convenient digital experiences.
Experience Verified Safety and Authenticity with Ace Ultra Premium
Are you looking for peace of mind when it comes to the safety and authenticity of your cannabis vaporizer disposables? As explored in our article on device authentication codes, establishing trust and preventing counterfeits are critical for secure access and product integrity. Many consumers worry about buying fakes or receiving low-quality products that could jeopardize their health or satisfaction. At Ace Ultra Premium, we address these exact concerns by using robust authentication features, lab-verified testing, and transparent verification procedures on every device you purchase.
Take charge of your experience today. Visit our main site at Ace Ultra Premium Co. to browse our selection of high-end, safe vape disposables. Check the detailed usage instructions and authentication steps for every product. Discover how advanced technology and rigorous lab testing can guarantee your safety and satisfaction. Shop now for premium, verified cannabis products you can trust.
Frequently Asked Questions
What are device authentication codes?
Device authentication codes are unique digital fingerprints that verify and authorize access to digital systems, ensuring that only legitimate devices can establish network connections.
How do device authentication codes enhance security?
They enhance security by creating multiple layers of defense against unauthorized access, requiring dynamic, device-specific verification that goes beyond traditional password systems.
What technologies are used to generate device authentication codes?
Device authentication codes leverage advanced cryptographic algorithms, machine learning, and hardware-specific signatures to create unique, secure tokens for each device.
In what situations are device authentication codes commonly used?
They are commonly used in securing smart home systems, protecting digital transactions, and safeguarding sensitive personal data against unauthorized access.

